Protecting digital footprints, while doing various online activities, is a major challenge in today’s ongoing era. Hackers and spies are constantly hunting for opportunities to get personal data and use it as they want. So, to elude various possible online threats, tracking, or cybercrimes we need to have robust cybersecurity software, which not only protects our personal data but also protects us from getting tracked or spying. So, today we are going to discuss various software solutions for cybersecurity. Let’s begin our journey.
Malwarebytes:-

Malwarebytes is a cloud-based suite, that offers anti-malware and cybersecurity solutions for personal and business consumers, it will help you to identify, analyze and remediate threats on a unified platform. The users of Malwarebytes are impressed by its various features like activity monitoring, antivirus software, getting alerts, data security, real-time monitoring, vulnerability scanning, user-friendliness due to intuitive design, and rootkit scanner. Rootkit Scanner is the standalone feature of Malwarebytes as it gives access to find difficult-to-detect malware, which can harm your devices or data in any possible manner. It has automatic repair of any system files and services that may be damaged due to any infection. It also provides you with a list of rootkits by scanning early, so that you can review them and take the best action. It has some pre-built integrations to make your work easier, such as Slack, ServiceNow, Datto RMM, IBM QRadar, and more. It has a 60-day money-back guarantee, in case you want to opt-out, out after taking the plan, but as it has a free trial, you can start with it, to understand whether it is fulfilling your requirements or not.
Bitdefender: –
Bitdefender is a cybersecurity solution that comes with licensing options to match the protection needs of businesses, data centers, and the public cloud. Its core features include activity monitoring, managing controls and permissions, antivirus, data security, real-time monitoring, and vulnerability scanning. Autopilot system includes various functions such as full parental control, hassle-free firewalls, spam filters, password management, file shredding, and more. It also provides a VPN but it is limited to daily requirements, you can upgrade your subscription to get the full benefit of a VPN.
Kali Linux: –
Kali Linux is one of the renowned and ready-to-use cybersecurity tools. It has hundreds of tools that companies can use to monitor networking systems for vulnerabilities. It is compatible with various devices and environments, as it is an open-source product with easy integration. It provides a huge set of pre-installed tools, which covers a wide range of security tasks such as network analysis, vulnerability management, password cracking, and wireless attacks.
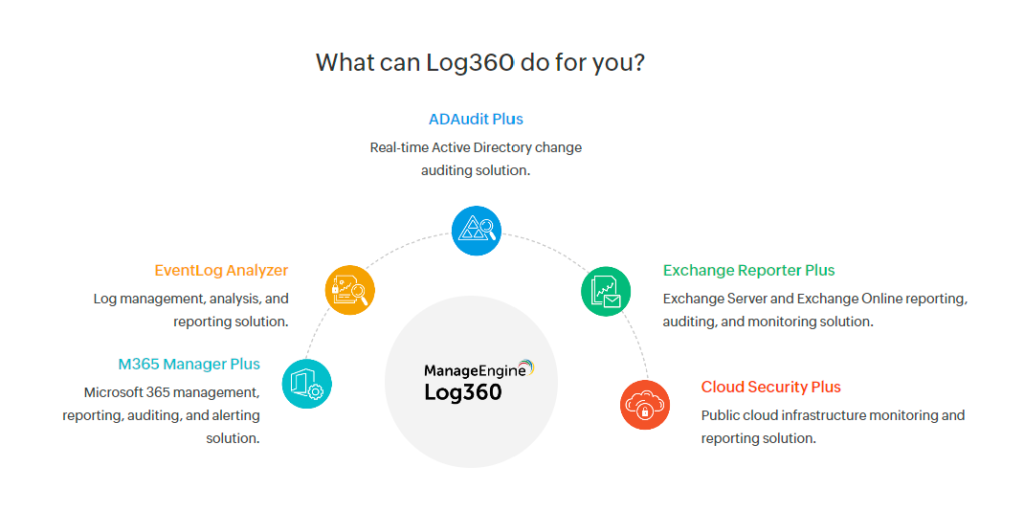
ManageEngine Log360: –
ManageEngine Log360 provides various solutions to a wide range of security needs. The platform helps its users to manage and analyze logs from various sources whether it is on-premises, cloud, or hybrid environments. It provides various functionalities such as SIEM, DLP, and CASB in a single place, which is the main reason for standing out from other competitors. Its various features include advanced security analysis, log management, real-time active directory change auditing, compliance management, data aggregation, alerting and reporting, and many more. It can easily integrate with various software like Microsoft Active Directory, Office 365, Google Workspace, AWS, Azure, Salesforce, and many more. The software is very prominent in providing threat detection, rule-based attack detection techniques, and responses with the help of machine learning-based anomaly detection.
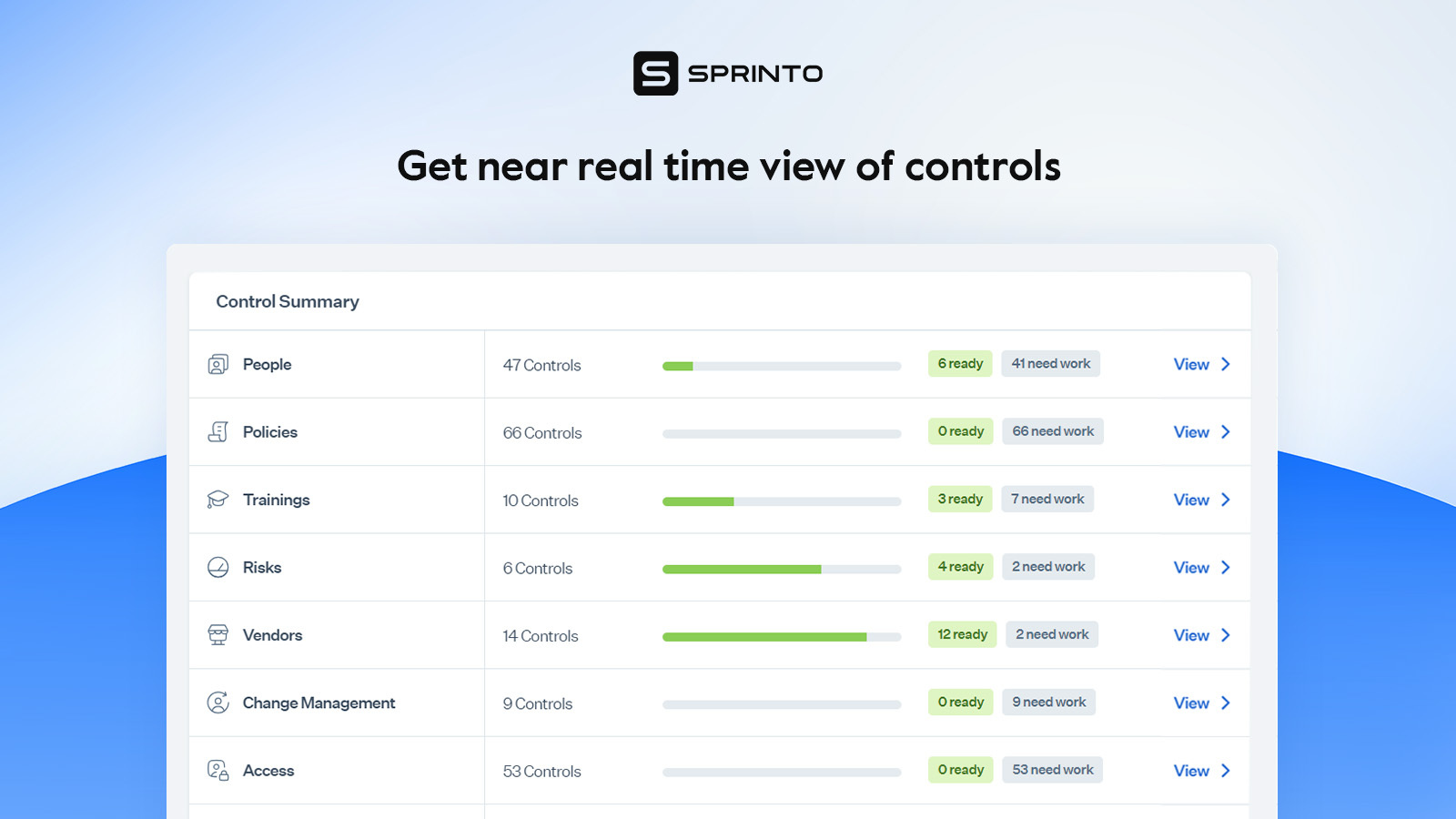
Sprinto: –
Sprinto is a cybersecurity and compliance automation tool for cloud-based companies. It helps to check out security gaps and implement control to remediate them. The key features of Sprinto include continuous control monitoring, audit success portal, managing access controls, vulnerability assessments, endpoint device security, centralized dashboards to verify security and compliance, and policy templates for hard security and compliance operations. It is an efficient compliance management information security platform for cloud-based companies. It has various pre-built integrations such as AWS, Google Cloud, Azure, ClickUp, Office365 and more. Its main advantages include strong compliance automation, audit access control, and responsive customer support.