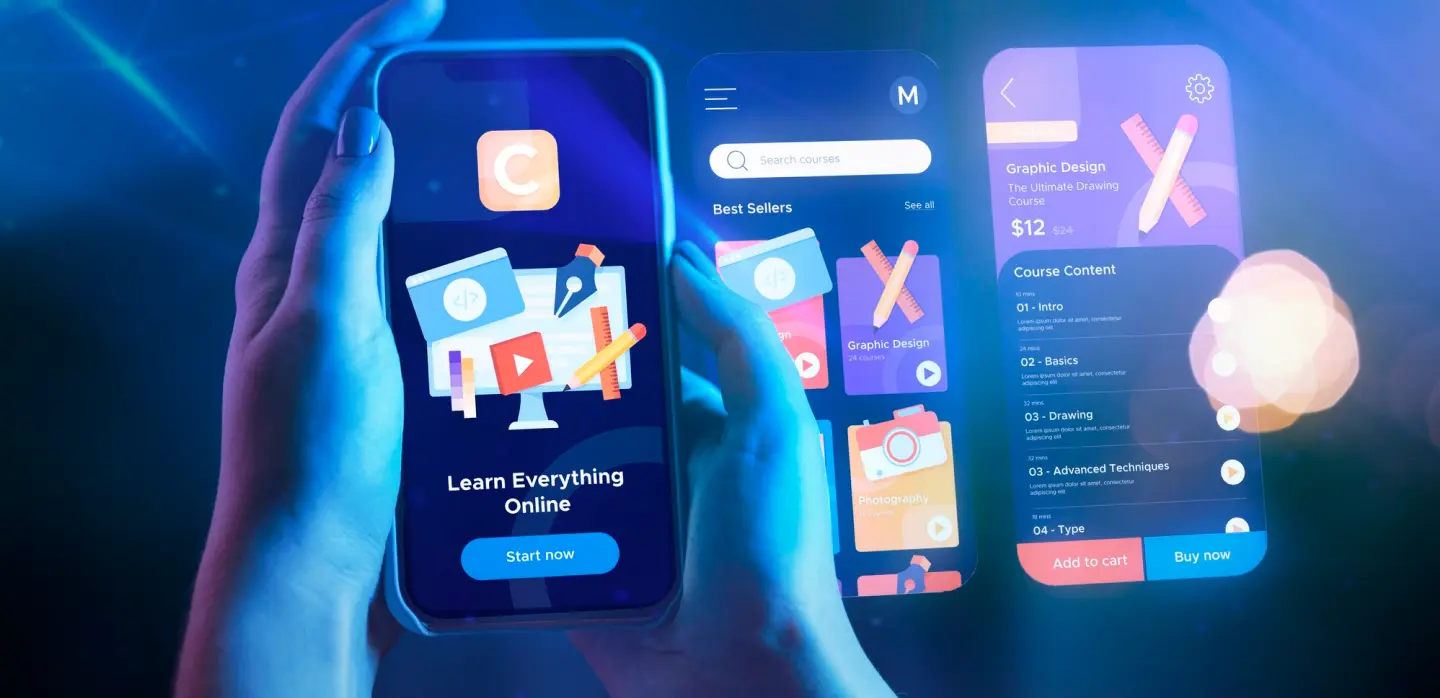
If we talk about that pilot tool, it simplifies the entire design process and makes the team work faster and smarter.UX Pilot is a design-driven AI tool that helps you seamlessly influence the user experience and UI user interface. It’s ideal for designers who want to create high-quality designs, wireframes and have a zero-user following. Whether you’re a designer or on a product team, you want to speed up your work; UX Pilot will help.
Core Features of UX Pilot:
AI-Powered Wireframe Tool:
UX Pilot’s AI-powered wireframer permits you to create wireframes for both desktop and portable right away. In seconds, you can investigate numerous plan concepts, making a difference you approve thoughts rapidly and proficiently.
Advanced UI Designer:
The high-fidelity plan motor changes over portrays or harsh concepts into pixel-perfect UI screens. This highlight empowers originators to make professional-level interfacing without broad manual work.
AI-Powered Design Chat:
UX Pilot incorporates a chat-based interface where you can control plans with straightforward content informational. You can rapidly alter components like colors, formats, buttons, and other UI components without repetitive manual altering.
Screen Stream and Client Journey:
You can create total screen streams and visualize the client travel as a model. This makes it simple to storyboard the client encounter and outline route ways productively.
UX Research & Smart Insights:
The stage helps in UX inquire about by recommending systems and creating context-aware meet questions based on your extend necessities. This guarantees that plans are user-centric and research-backed.
Figma to Code Workflow:
AI-generated UI plans can be traded straightforwardly to Figma for collaboration.
Code-ready screens are created, making engineer handoff consistent and error-free.
Rapid Prototyping:
From concept to demonstrate in reasonable a few clicks, UX Pilot supports multi-platform plans for both flexible and desktop, allowing bunches to quickly test and emphasize contemplations.
UX Pilot: Future-Ready Design
UX Pilot is changing cutting edge UX and UI plan by combining capable AI computerization with designer-focused instruments. It rapidly turns thoughts into wireframes, high-fidelity screens, and total client ventures, making a difference groups work quicker with more noteworthy clarity. With natural-language commands, creators can alter formats, colors, and components easily, lessening tedious assignments and boosting imagination. Its smooth Figma integration and code-ready screens make collaboration and designer handoff astoundingly effective. Whereas minor confinements exist, UX Pilot’s speed, precision, and keen plan proposals make it a standout arrangement for anybody looking to raise their workflow and make high-quality advanced experiences.
Advantages and Drawbacks:
Advantages:
No time wastage because ideas are visualized quickly and then you can easily apply them.
Standard UX makes it a fast and organized way to launch frameworks.
It’s also useful for Figma integration and simplifies the handoff of developers.
Drawbacks:
If we talk about its limitations, the AI doesn’t always follow your guidance.
Some users also say that generating multiple scripts quickly leads to a loss of credit.
It’s been observed that subscription cancellation or refund issues occur frequently.
Conclusion:
Nowadays everyone is busy in their life, no one wants to waste much of their time, which saves time and also improves the quality, UX Pilot simplifies UI design by using AI.Friends, UX Pilot is an AI tool useful for UI designers, whether they’re on product teams or design professionals. It helps build wireframes, visualize user journeys, and export them to Figma. UX Pilot is useful for UI.